Home » IT Services » Security Assessment and Compliance » Cloud Security Audits
Cloud Security Audits
As technology advances, every organization wants to move services to the cloud for better access, excellent performance, and optimized hardware costs. Our specialized cloud audit service evaluates applications and services hosted in cloud environments, checking their infrastructure, data, and applications to ensure that they are secure.
AWS Cloud Audits
eNoah’s cloud audit specialists will do periodical AWS audits to ensure security configurations are in line with all the required security standards. An independent AWS security audit offers you the opportunity to identify unwanted IAM users, roles, groups, and policies, making sure that your users and software only have the permissions they are required to have.
Our audit reports help customers to validate:
- Security implementation status across various AWS deployments
- AWS awareness on security events within the organization
- Compliance based on AWS configurations


AZURE Cloud Audits
Based on experience from around the globe, our AZURE security audit uses an extensive array of security configurations provided by Microsoft. This exhaustive audit, based on industry standard recommendations, identifies gaps in configuration implementation and logs defined security policies and mechanisms to help you meet all the required standards.
This security audit helps teams to:
- Identify the current status of security implementations
- Determine what has to be done to meet industry standard recommendations
- Look at the compliance index based on standard AZURE controls
Cloud Security Audit Process
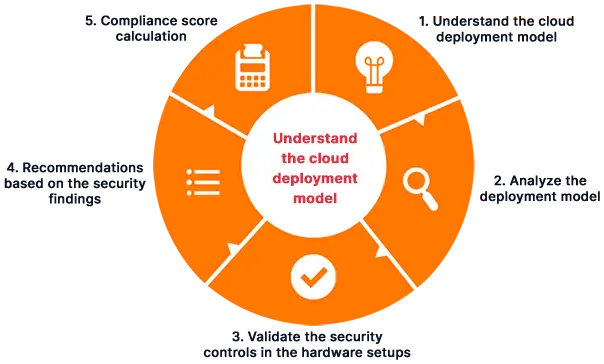
- We conduct dedicated sessions to get a clear understanding of the client’s infrastructure and cloud deployments
- We analyze your cloud deployment model and compare it to industry-standard recommendations
- We use an exhaustive checklist to validate hardware setups and implementations under defined categories
- We calculate and share a detailed compliance score that covers different categories
- Based on our findings, we propose recommendations for improvement
Get in Touch
Interested in learning more about our Cyber Strategy and Governance? Contact eNoah today to discover how we can help your organization achieve its automation goals.