Home » IT Services » Security Assessment and Compliance » Compliance Management and Audits » ISO 27001 Information Security Management
ISO 27001 Information Security Management
ISO 27001 is the industry’s standard to provide requirements for an Information Security Management System (ISMS). An ISMS is a methodical approach to managing a company’s sensitive information so that it remains secure. It applies risk management processes to people, processes, and IT systems, helping businesses in any sector to keep information assets secure. ISO 27001 uses a top-down, risk-based methodology and is technology-neutral.
Organization Pain Points in Implementing Information Security
- Lack of defined protocols for information governance, risk, and compliance
- Continuous information reporting and documentation
- Proper information asset categorization and management
- Lack of defined protocols for information security verification and validation
- Detailed information risk assessment and reporting

How eNoah’s Expert Team Can Help
- Assign roles and responsibilities
- Top management
- Information security steering committee
- Information security officer/manager
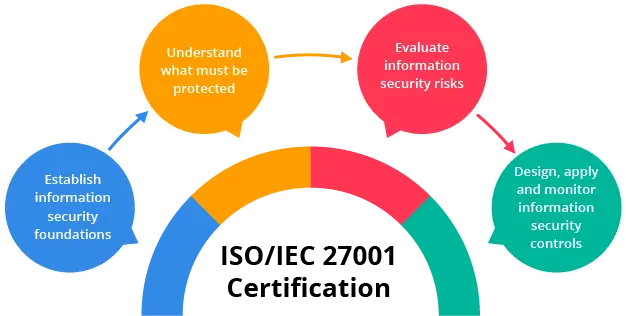
- Identify controls to be implemented and set up an information security plan
- Manage the information security plan
- Control and monitor information security
- Identify which other assets are used
- Understand the connection between information and other assets
- Understand the value of assets
- Evaluate the type of context in which the organization works
- Identify which controls are already in place

Value Proposition
Secures your information in a defined process
- An ISMS helps protect all forms of information, including digital, paper-based, intellectual property, company secrets, data on devices and in the Cloud, hard copies, and personal information.
More resilient against cyber attacks
- A well defined and maintained ISMS will increase the organisation’s resilience to cyber attacks.
Protects confidentiality, availability and integrity of data
- With defined policies, procedures, technical and physical controls in ISMA will help protect the confidentiality, availability and integrity of information.
Reduces costs associated with information security
- Detailed risk assessment and analysis approach of an ISMS, it helps organisations to reduce the cost on adding technology to improve security infrastructure
Provides a well defined framework
- ISMS provides a very well defined framework for the organisation’s information safety and management
Get in Touch
Interested in learning more about our ISO 27001 Information Security Management? Contact eNoah today to discover how we can help your organization achieve its automation goals.